GitLab Agent Server Unauthorized error
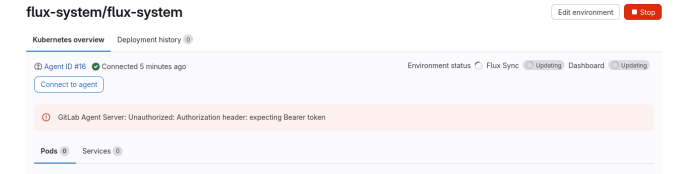
Without going into detail about how exactly and why everything is organized, access is provided through the following chain:
1 | |
The Main Frontend manages the gitlab subdomain, which is closed to external access via auth_basic authorization.
Authorization on the /-/kubernetes-agent/ socket in gitlab itself occurs via a json/graphql payload.
But the Main Frontend also passes the state of the $remote_user field to the socket.
Accordingly, GitLab attempts to perform authorization based on Basic, but not on the parameters in the json/graphql payload itself.
And we get an error:
1 | |
My biggest mistake
Of course, the second thing I did was disable authorization for my external IP address.
This was obvious since Authorization header: Bearer error was indicated.
But it didn’t work, I thought then.
After that there were a lot of deployments, reinitializations, configuration changes.
But even that didn’t work.
The devil is in the details
Inattention to obvious details led me a couple of days later to the Nginx log in the GitLab instance again.
In the log I noticed my login $remote_user from auth_basic passed from Frontend, which shouldn’t be there.
So what’s the mistake?
Let’s say you have auth_basic authorization enabled. The browser sends the Authorization: Basic header, since you entered your login and password to connect.
You disable authentication. Verify that it’s truly disabled, for example, using curl or wget.
However, when you refresh the page, or even open new tabs for this site, the browser continues to send the Authorization Header until you close and reopen it.
I just had to reopen the damn Fox!
Solution to the problem
1 2 3 4 5 6 7 8 9 10 11 12 | |
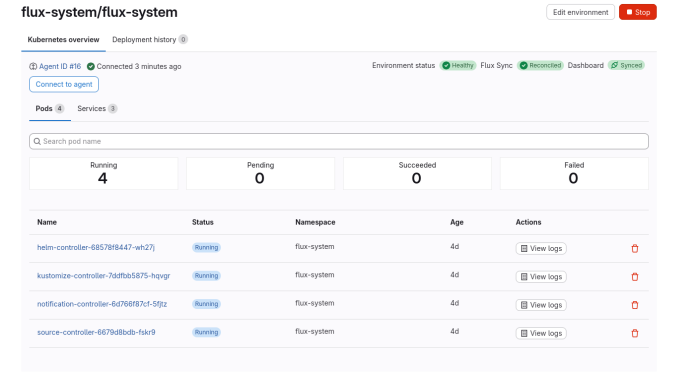
Authorization is enabled, everything works correctly.
Original post on SecOps.it Blog • GitLab Agent Server Unauthorized error